Welcome to part 10 of a multiple part course on passing your AWS Architect, Developer & Sysops Associate exams. The best part…this course is totally free of charge!
If you’ve been following my series on VPCs then by now you’ll have a decent understanding of what one is. In our first article we learnt the basic concepts of VPCs and in the second we built a VPC using both the VPC wizard and totally from scratch.
In this article we take a deep dive look into Network Address Translation or NAT for short. We will examine the two flavours of NAT available on AWS. NAT Instances & NAT Gateways. It’s important to have a working knowledge of both and the reasons why you would choose one over the other.
What is a NAT? Network Address Translation (NAT) is a means for resources that reside in private subnets to access the internet in a secure fashion. They come in 2 flavours. NAT Instances which are user maintained and NAT Gateways which are managed by AWS.
A typical reason for wanting this functionality would be for updating software running on instances that reside within a private subnet.
The article will take just 10 minutes to read and after doing so you’ll have all you need to know to answer any basic question around NAT gateways & instances to pass the AWS certifications.
Who should read this?
If you are studying for the:
- AWS Associate Architect
- AWS Associate Developer
- AWS Associate SysOps
Or you are using AWS and want to learn more about NATs then this is the article for you.
NAT Gateway vs NAT Instance – Overview

Right, let’s get into it.
The first and most logical question you’ll be asking yourself and what most likely led you to read this blog post is what are the differences between NAT Gateways and NAT instances. After that you’re next question is probably going to be which one should I use?
The second question is easy to answer. You should use NAT Gateways.
Why so easy to answer? In short, NAT instances are on their way out of regular use. Gateways were specifically designed to replace them and be easier to use. We’ll go into the details of exactly why you should use gateways as opposed to instances later in this article.
We’ll also look at how to create a NAT gateway & instance.
Keep reading and I’ll show you how…
Availability
NAT gateways are highly available. If you create NAT gateways across multiple availability zones then your instances we continue to be served even if one gateway fails.
NAT instances can achieve high availability but you’ll have to write a script to handle the failover when it occurs. This increases the complexity compared to simply creating multiple NAT gateways across AZs.
Bandwidth
NAT gateways each have a bandwidth limit upto 45Gbps, where as NAT instances are totally dependent on the instance type they run on. t2Micro will have a smaller bandwidth allowance compared to a t2Medium.
Maintenance
NAT gateways require no maintenance as they are managed by AWS as a service. NAT instances on the other hand require updating for operating systems, software patches, virus updates etc….
Performance
There’s a clear winner with this, in that NAT gateways are specifically designed for this purpose and are optimised to handle nat traffic. Where as instances are a generic linux AMI that is configured to handle nat traffic.
Bastion Servers
While most of the points I’ve highlighted learn in favour of gateways, there are a few exceptions and bastion servers are one of them. Currently gateways don’t support this, where are instances do. So if you want a bastion server then in this specific case an nat instance may be the way to go.
Private IP Addresses
For nat gateways AWS will automatically select an IP from the public subnet that this nat gateway is assigned to. No configuration is required.
For nat instances, we are essentially creating a EC2 instance and assigning it to a subnet, at this point an IP address is created.
Either way the configuration is low regardless of the nat type you chose.
Public IP Addresses
NAT gateways only give you the option to assign an elastic IP address. You’ll have to create one in the EC2 dashboard of course.
For nat instances, you have a few more options since it is essentially an EC2 instance you’ll get both a public IP address and you can also assign a elastic IP to the instance. The elastic IP address would be the prefered option. Because your public IP can change, for instance if you were to restart the server the IP may change.
Cost
This comparison inevitably becomes a scale. It’s totally dependent on the number of gateways or instances you have. In addition other factors such as the throughput and where instances are concerned, the size of those instances. I.e. the larger the instance the costlier it is to run.
More info
I’ve covered about half of the points here that describe the differences between nat gateways and instances. If you want to know more, then AWS have written a comprehensive article going into more detail about those differences here.
Network diagram of NAT Gateway VPC example
Ok before we go any deeper, I thought I’d break down what a typical VPC looks like with a nat gateway installed.
If you want a more indepth review of the parts of a VPC intro blog for more detail about the other parts of a VPC then checkout my post on introducing a VPC.
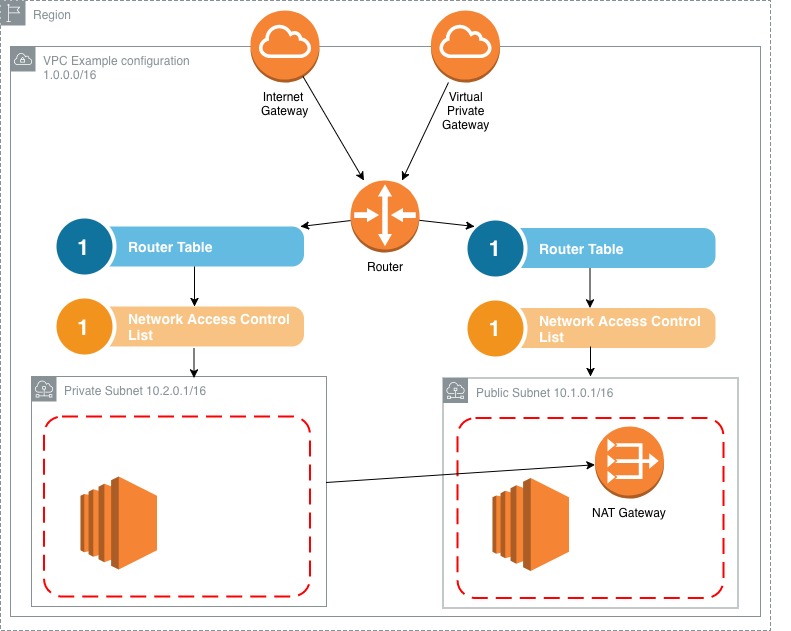
Notice that the nat gateway sits in the public subnet and provides a connection to the instances in the private subnet.
What is NAT gateway
By now you should be getting a sense of what a NAT gateway is. But let’s briefly go over the basics just to clear up any ambiguity.
NAT gateways were created specifically to replace and address the shortcomings of NAT instances. They are completely managed by AWS and require a lot less setup and maintenance compared to a traditional nat instance. If you’re in doubt as to what to chose then theres a high likelihood that gateways are the best option.
I’ll go into detail about the benefits of NAT gateways in the What are the benefits of NAT gateways section.
How to create a NAT gateway
Ok, let’s quickly go through the steps required to create a nat gateway.
Created on the VPC dashboard rather than the EC2 one since they are managed by AWS.

So just click on the nat gateway option in the dashboard.

There is a wizard for creating a NAT Gateway which guides you through the process.
Select the public subnet from the list
Allocate a elastic IP address (you’ll need to of created this prior to setting up your gateway)
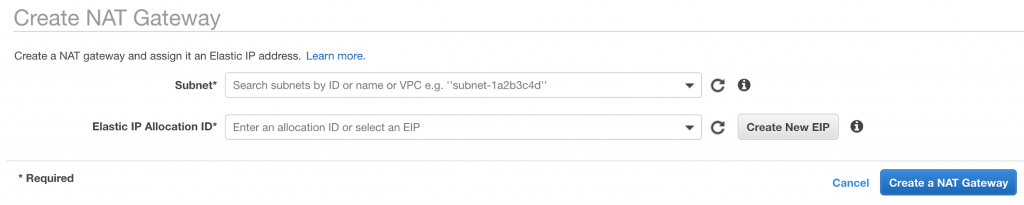
Hit create and wait. It takes roughly 15 minutes usually for nat gateway to startup.
Go to the nat gateway dashboard and you should see your newly created instance.
Click Add Route.
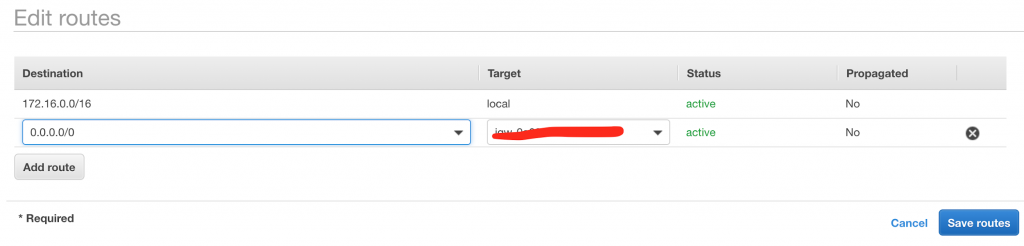
Set the destination to be 0.0.0.0/0 and the target to be the nat gateway. (the 0.0.0.0/0 basically means all traffic)
And that’s it. You’ve set up a nat gateway.
NAT gateway pricing
Pricing like almost all AWS services tends to be on a per usage basis. From reviewing the AWS pricing chart that price tends to vary between regions. But basically the price ranges between $0.045 per hour and $0.093 per hour.
This is of course, per instance. The more instances you add the more you pay!
What the the benefits of NAT gateways?
Maintenance for gateways is relatively low, you don’t need to worry about operating system patches or virus updates. All of this is handled by AWS automatically.
Gateways are prefered by the industry as a whole. You’d need a pretty specific reason not to use them and choose an instance instead.
The bandwidth problems that you are likely to encounter with instances are highly mitigated when using gateways as they scale up to 45Gbps.
With gateways, you don’t need to associate them with security groups. This is because a nat instance is basically an EC2 image setup for nat usage and a gateway is preconfigured to operate specifically as a nat.
Where a nat instance would inherit the rule set around IP allocation from the subnet it resides in. With a gateway you automatically get assigned a public IP address.
You can achieve high level of redundancy with gateways simply by creating them across multiple availability zones in your region. This way if one fails then the others will carry over automatically. Instances require more configuration for this.
Gateways don’t have the additional configuration checks such as disabling source destination checks. You will have to do this for instances.
You can’t and shouldn’t need to SSH into your gateways. Further increasing security on your system.
And just in general, following that point. Gateways are more secure than instances.
What is NAT instance
NAT instance is basically a EC2 instance with a specific AMI (Amazon Machine Image) that is designed for handling NAT style traffic. It’s the older of the 2 solutions available for handling situations where NATs are required.
The typical setup of a NAT instance involves creating an instance on the EC2 dashboard, associating it with your VPC and finally the subnet. I’ll go into detail in the next section on how you create a NAT instance from scratch.
How to create a NAT instance
Ok, let’s quickly go through the steps required to create a nat instance.
First off we head to the EC2 dashboard and create a new instance.
From the pre configured AMI list select the NAT instance type.
Next we need to select the VPC that this instance resides.
Chose a subnet that is public to place the nat instance in.
Assign a security group to the instance. For obvious reasons it will have to have at least http/https & ssh access.
Create the instance and then proceed to the EC2 dashboard
Right click on the instance and disable source destination check. You need to do this otherwise it won’t work as a nat instance.
Next we need to go over to the VPC itself. Access the route table. We want to set a route out the route table associated with our private subnet out via the NAT instance we have created. Add the route as shown below.
Click Add Route.
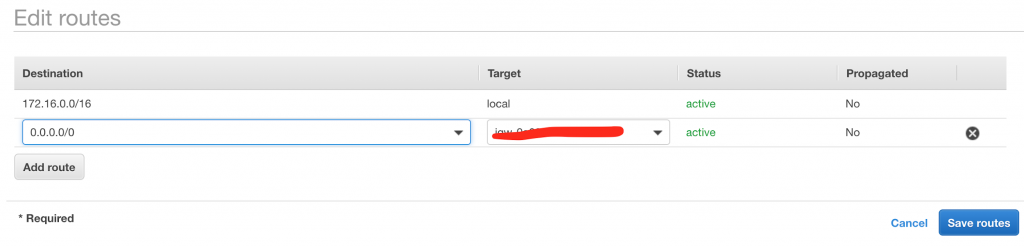
Set the destination to be 0.0.0.0/0 and the target to be the nat instance. (the 0.0.0.0/0 basically means all traffic)
And that’s it. You’ve set up a nat instance.
What are the downsides to NAT instances?
There’s a whole bunch of issues you have to take into account when using nat instances. Here’s a few to be aware of:
Bottlenecks: And there are lots of these to take into account. Instance size for example is something you will have to take into account. You will likely have to over provision large (and expensive) instances for your nat gateways to handle sufficient throughput of traffic.
High Availability: Configuring high availability for nat instances usually involves more work when compared to gateways. You don’t get it out of the box. If you’re instance goes down then you’ll lose internet access for you instances connected to it.
Bandwidth: Is totally dependant on the instance size you provision for your nat instance. This closely relates to the bottleneck point I made earlier. t2Micros will have a smaller bandwidth allocation compared to a t2Medium for instance. Also you have to ask yourself the question, what happens if your system exceeds the bandwidth allocations?
Scaling is harder: Continuing on the theme of bottlenecks, what do you do if your system needs to scale with demand? You’ll have to place you instances behind auto scaling groups to grow and shrink as demand changes. This further complicates usage of nat instances.
Updates: as a nat instance is user maintained, you’ll have to update the operating system with new patches when required and also things like virus checkers. This adds to system maintenance.
Gateways are preferred: if for whatever reason you decide to go with an instance, then the general industry preference is for gateways. You’ll find yourself having to come up with pretty strong justifications for choosing them above a gateway.
Exam Tips
A few things to note when taking the aws certifications:
For nat instance, you must remember to disable source/destination check for each nat instance.
NAT gateways/instances must be placed in public subnets.
You’ll need to configure the routing table of the private subnet to receive traffic via the nat gateway/instance.
You bandwidth for nat instances is limited by the size of the instance it’s running on.
You can achieve high availability from a nat instances via auto scaling groups and you can achieve high availability from nat gateways via multiple availability zones.
Additional questions:
aws nat gateway vs nat instance pricing – which is cheaper? This entirely depends on the amount of usage. But if you compare like for like, then gateways are more cost effective.
Nat gateway instance high availability – high availability is easier to achieve via a nat gateway than a nat instance. It is also much easier to maintain.
Nat gateway vs internet gateway – two different things that shouldn’t be confused. A internet gateway provides access to the internet for your entire VPC. Where as a gateway provides internet access for a subnet.

